Thanks to Simon Dingle, I'm going to be getting into the world of Android. One of the things that shocked me over the first few days, was the large number of applications that came bundled with the phone that could not be uninstalled, and had persistent background processes. In the "direct consequences" camp, the Motorola News and Gallery application simultaneously chewed my bandwidth and flattened by battery, in the more worrying "shady unknown consequences" camp, an app call "Arabware [1]" offered to "localize" my services, and also could not be uninstalled or stopped. I decided it was time I got root.
The official guides for how to root a Motorola Atrix 4G on the latest update (2.3.4 at the time of writing) are laughably naive. In 5 minutes I could easily find 50 sites all parroting the same process involving complex and dangerous flashing of firmware. The first bit of mis-information that needs clarification, is that despite the Motorola 2.3.3 developer preview having an unlocked bootloader, the official 2.3.4 Gingerbread update from Motorola DOES NOT HAVE AN UNLOCKED BOOTLOADER. No problem they say, just flash this firmware in this ZIP file, supposedly extracted from a Chinese leaked version of 2.3.3. What?! You want me to flash fimware passed around as a zip file from random locations? Not a chance. To make it worse, after a quick squiz at the .sbf file, I found this comment embedded in it:
"The2dCour, known troll in your phone."Awesome. Not a chance I'm touching that.
Here's a much safer, simpler way to root your device, which involves no warranty-voiding, security-spine-chilling hoop jumping.
All I wanted was root. I'm familiar enough with Linux to make my way after that. If you're "non-technical" then move along :) The steps are:
- Put your phone into USB debugging mode.
- Download and install the Android Debugging tool from the Android SDK.
- You'll need to run the SDK executable (android) and install the "Platform Tools" to get ADB these days.
- Plug your phone into your computer.
- Run "adb devices". You should see the serial number of your phone appear.
- Download the binary zergRush exploit from it's developers. The source code is also available for you to examine (or compile).
- Upload it to your device with "adb push zergRush /data/local/tmp".
- Connect to your device with "adb shell"
- In the shell, switch to the temp dir and run zergRush "cd /data/local/tmp/; ./zergRush"
- You should see the following (the image below has been partially redacted):
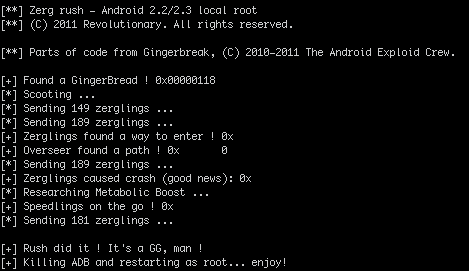
- If you get the "Killing ADB and restarting as root" line, then it's worked. Exit your adb shell and reconnect. You'll see a "#" as your prompt indicating you're root.
And that's it. On the one hand, I'm happy there's a "safer" easy way to get root on my own device, on the other hand, I'm uncomfortable with the fact that one of Motorola's flagship phones can be 0nwed so easily, with no update forthcoming.
[1] Yes, I know Arabware is a localisation service for the Arabic alphabet. I'm not saying it's shady, just that I see no reason why it should be a mandatory app in South Africa.

